Imagine you want to visit your online banking website «www.example-bank.ch». Now, instead of getting the correct IP address your computer gets manipulated information and connects you to a website that is owned by a criminal. You wouldn’t notice but disclose your online banking credentials to the attacker.
Luckily, DNSSEC is here to help. The extension of DNS protects you from being misled and helps you reach exactly the address you typed into your browser. A complex cryptographic process makes sure, that you’re always at the right place.
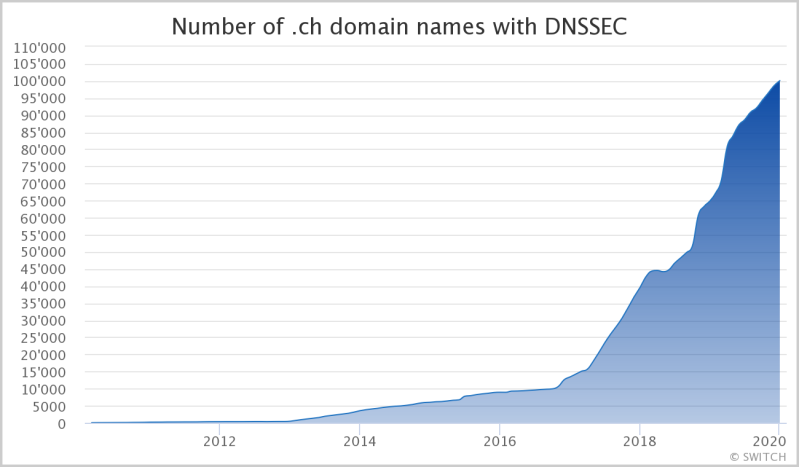
100’000 .ch domain names are signed with DNSSEC
In late December 2019 the .ch zone achieved a milestone with 100’000 DNSSEC secured domains. DNSSEC adds digital signatures to DNS answers and helps to mitigate attacks on DNS name resolution.
The percentage of .ch domain names that are signed is still below 5%, but is rising thanks to a few registrars like Infomaniak, OVH, Firestorm and netzone that sign domain names for their customers by default. The number of DNSSEC signed .ch domain names rose 54% from 1.1.2019 to 1.1.2020.
Top .ch domain names are just average regarding domain name security
Continue reading “100’000 .ch domain names are secured with DNSSEC!”


