When people hear about IPv6-specific security issues, they frequently tend to rate this as an argument in favour of delaying or avoiding IPv6 deployment on their enterprise or campus network. Even without IPv6 being consciously deployed, however, some of the IPv6-related security issues were already introduced to most networks many years ago. The reason for this is simple: IPv6 is implemented in all common operating systems and enabled by default. We introduced hosts with these operating systems on our networks several years ago – be they clients on the office network or servers in a data centre or DMZ.
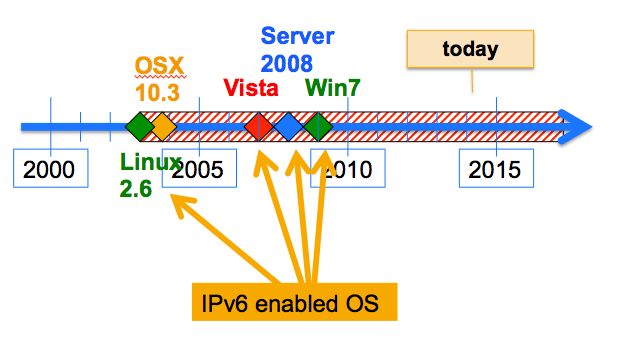
Since most, if not all, of today’s company networks are IPv6-enabled to a certain degree, they are attackable over IPv6. To make things worse, in contrast to IPv4, IPv6 brings along different kinds of autoconfiguration functionality, which can be misused. Network operators and security people who have neither basic IPv6 experience nor measures in place to detect IPv6-related attacks run a risk, and this risk is permanently increasing as the bad guys have already started to use IPv6. Bad guys are usually early adopters.
Continue reading “IPv6 insecurities on “IPv4-only” networks”
